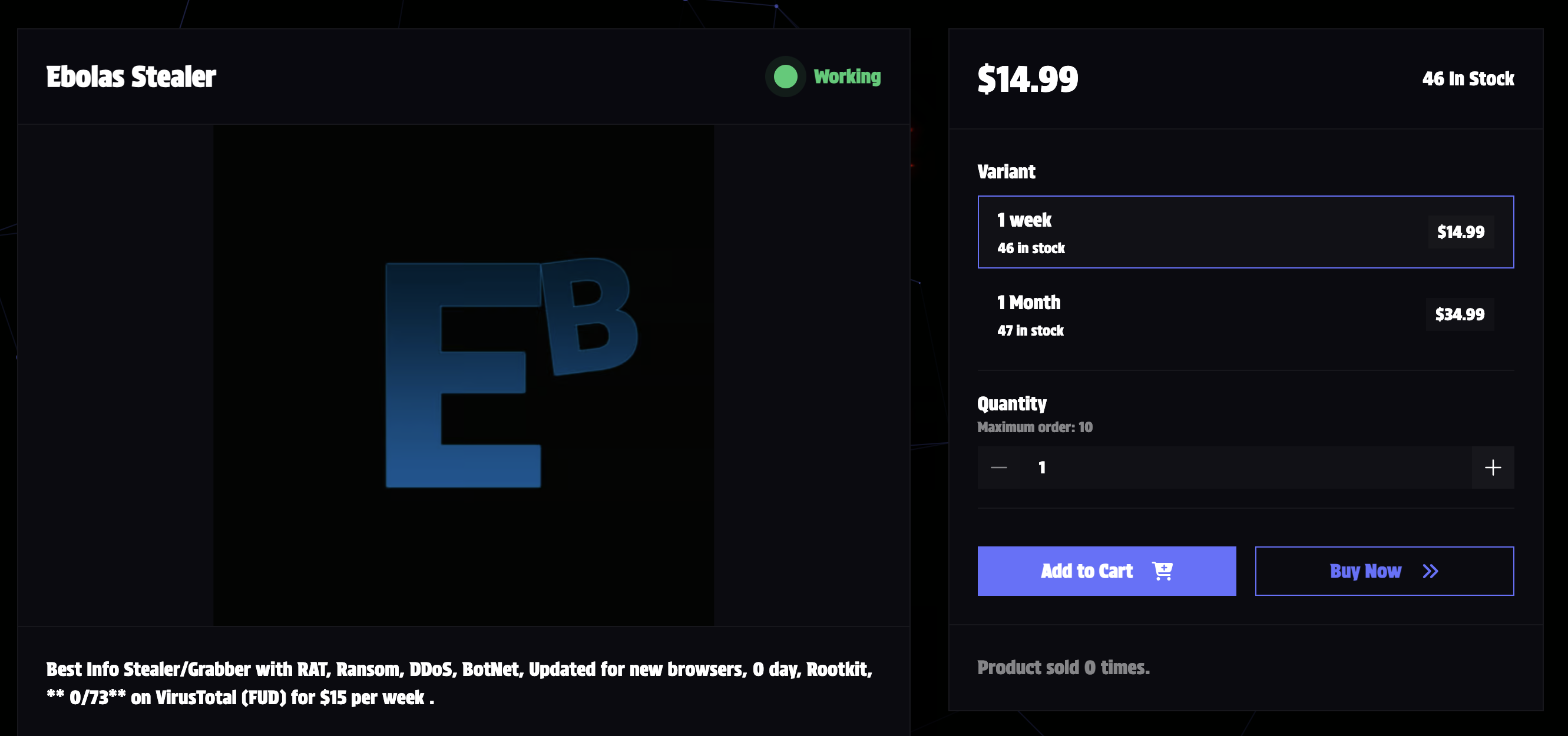
Introduction
Ebolas Stealer is a new hybrid malware combining infostealer, RAT, and ransomware capabilities into a single package sold for just $15/week.
The author claims it's fully undetectable (0/73 on VirusTotal), though such claims should be treated with caution. What makes Ebolas concerning is its low barrier to entry and comprehensive feature set.
Warning: This article is for educational purposes only. Always conduct security research in isolated environments.
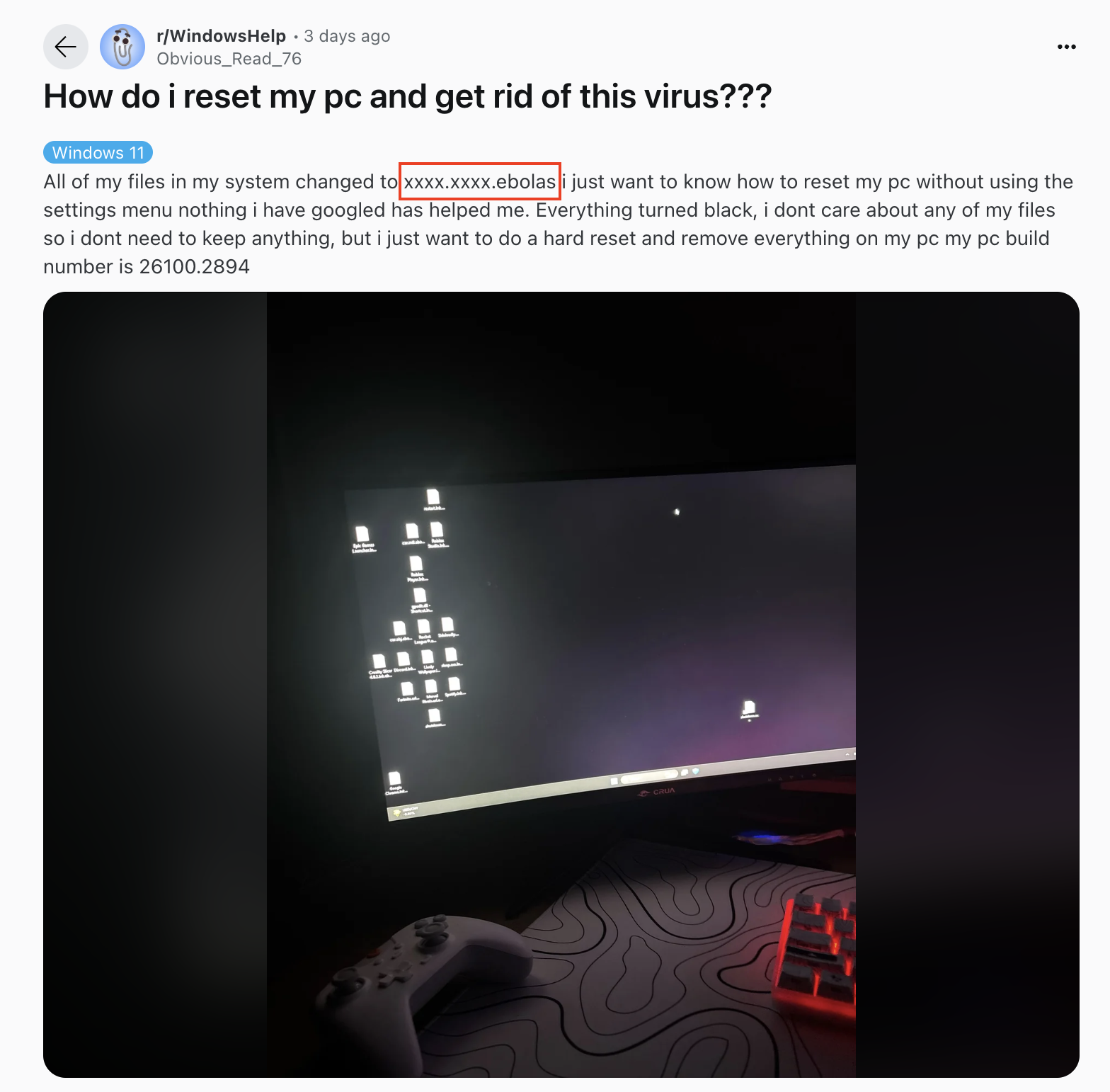
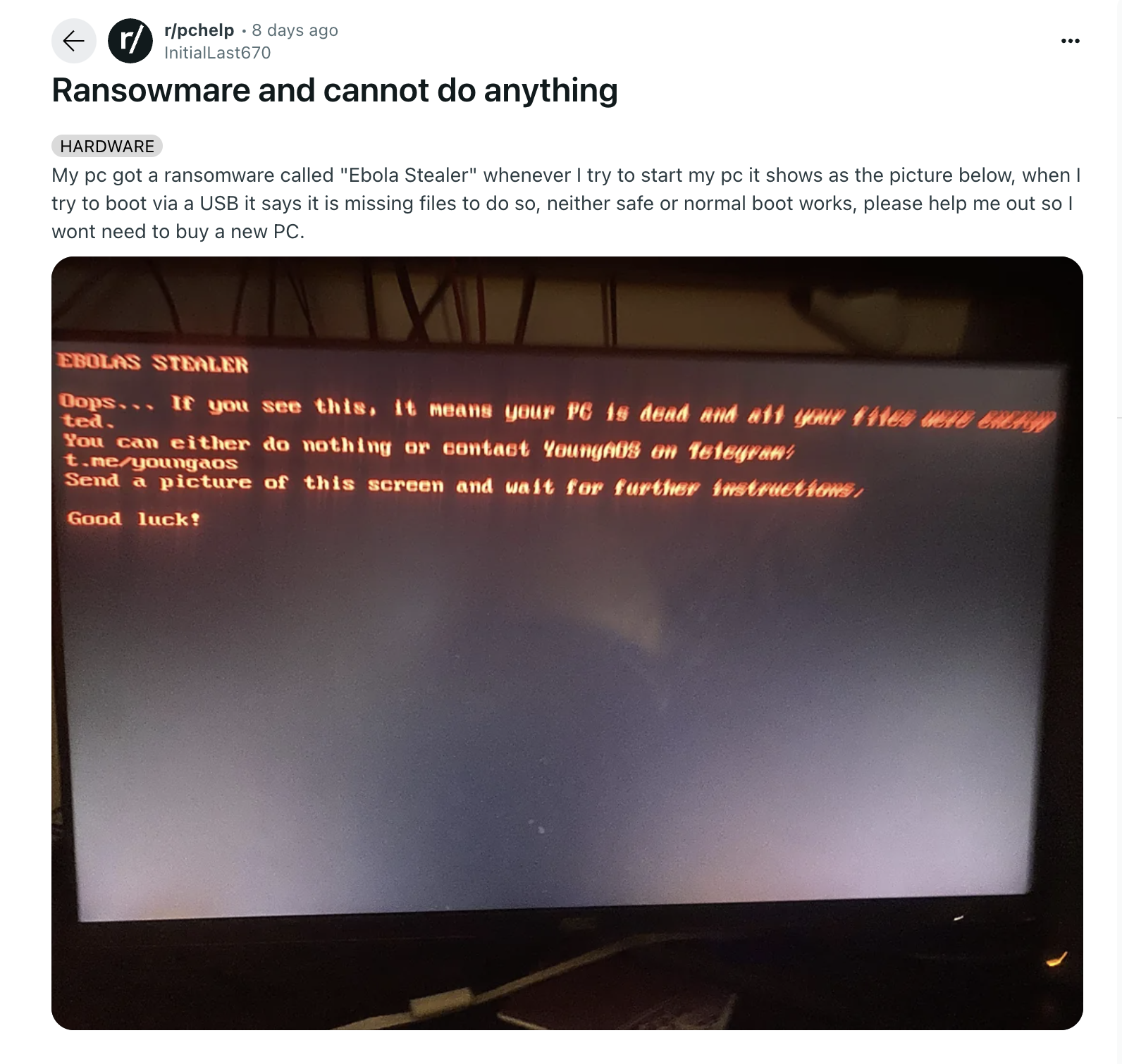
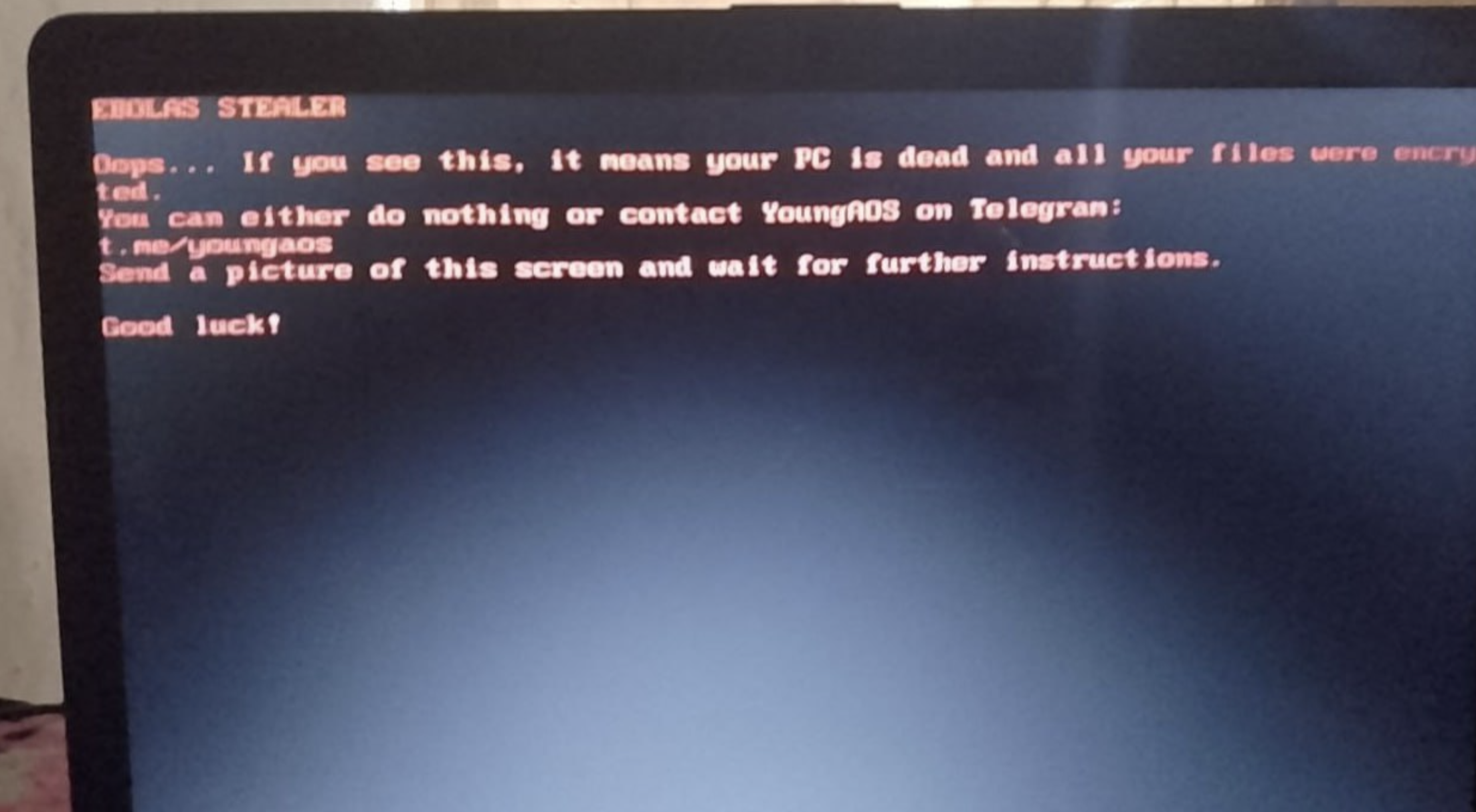
Ebolas infections have already been observed in the wild. Reddit users have reported encrypted files and ransom notes:
Discovery
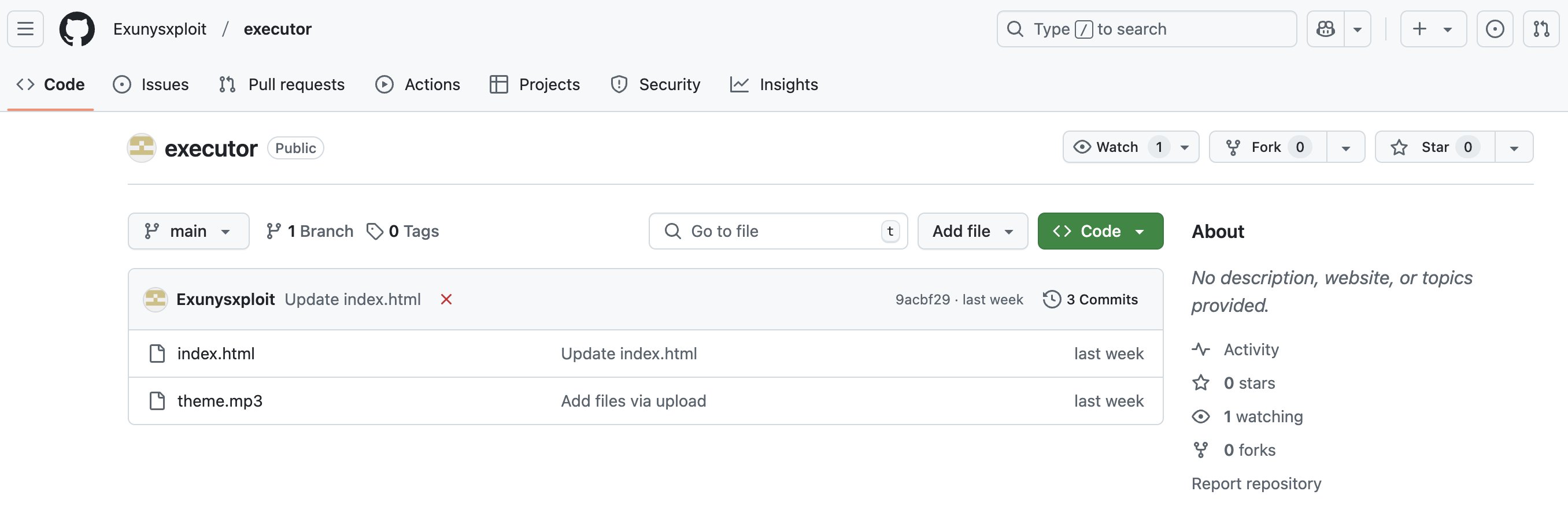
I first encountered Ebolas on GitHub, where threat actors were distributing it as a fake Roblox cheat impersonating Exunys, a legitimate cheat developer. The malicious executable has since been taken down.
Note: A detailed malware analysis is in progress. This article will be updated with IOCs and technical findings.
Tactics, Techniques, and Procedures
| Tactic | ID | Technique |
|---|---|---|
| Initial Access | T1566 | Phishing (Discord DM Spreading) |
| Persistence | T1547 | Boot/Logon Autostart Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1027 | Obfuscated Files |
| Credential Access | T1555 | Credentials from Password Stores |
| Collection | T1005 | Data from Local System |
| Exfiltration | T1567 | Exfiltration Over Web Service |
| Impact | T1486 | Data Encrypted for Impact |
Features & Capabilities
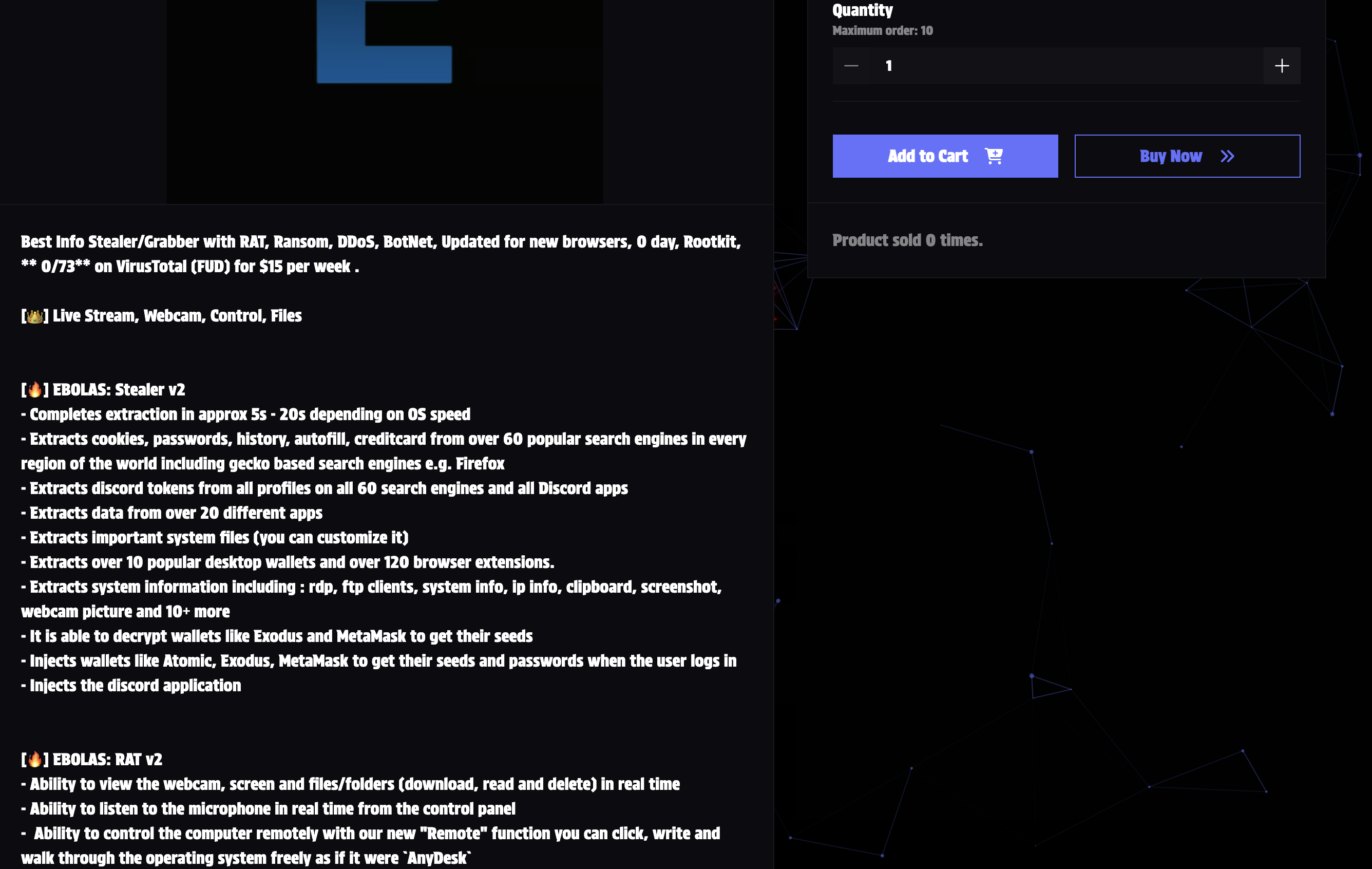
Infostealer
- Fast extraction (5-20 seconds)
- Targets 60+ browsers cookies, passwords, autofill, credit cards
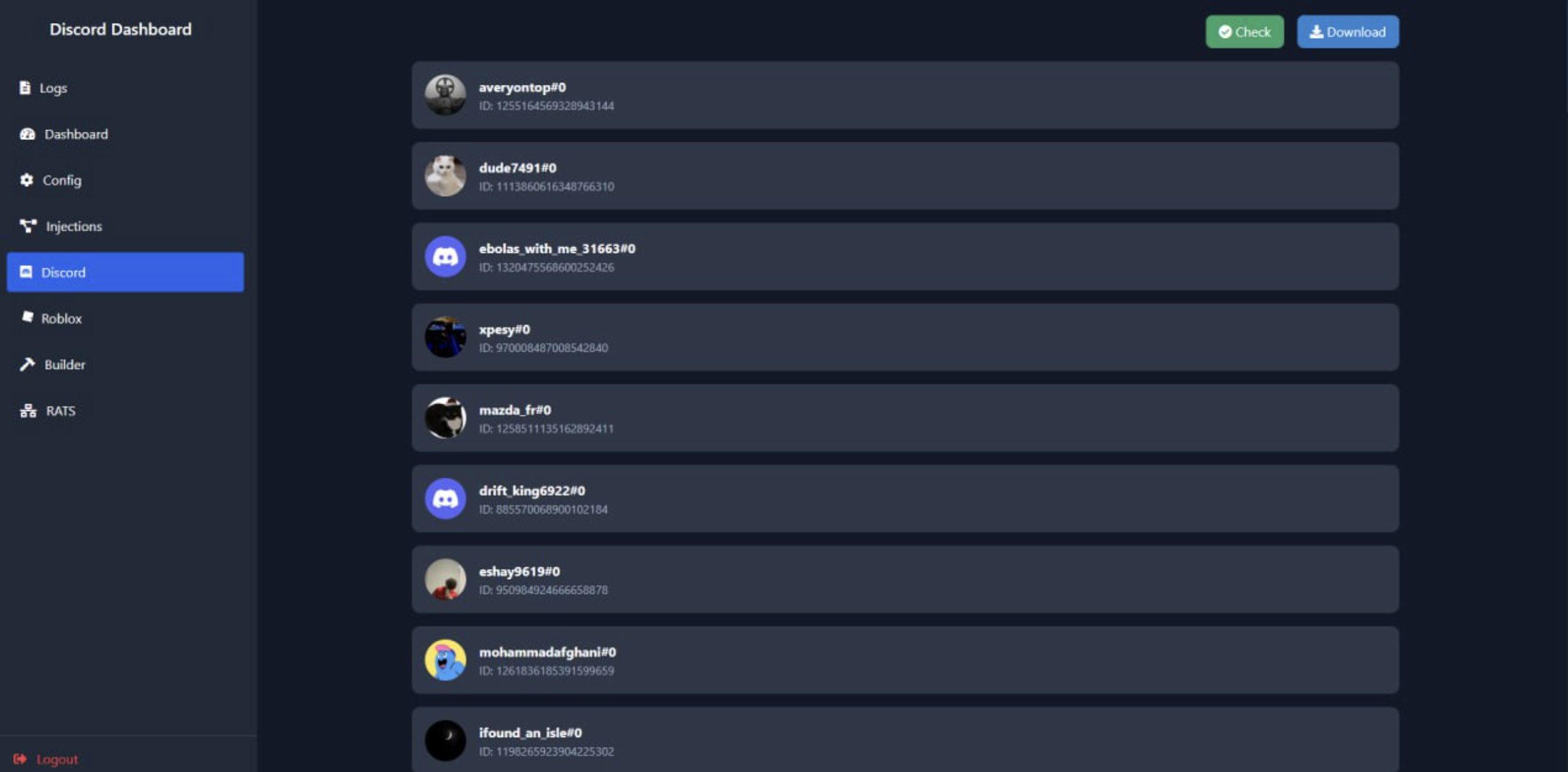
- Discord token theft across all profiles
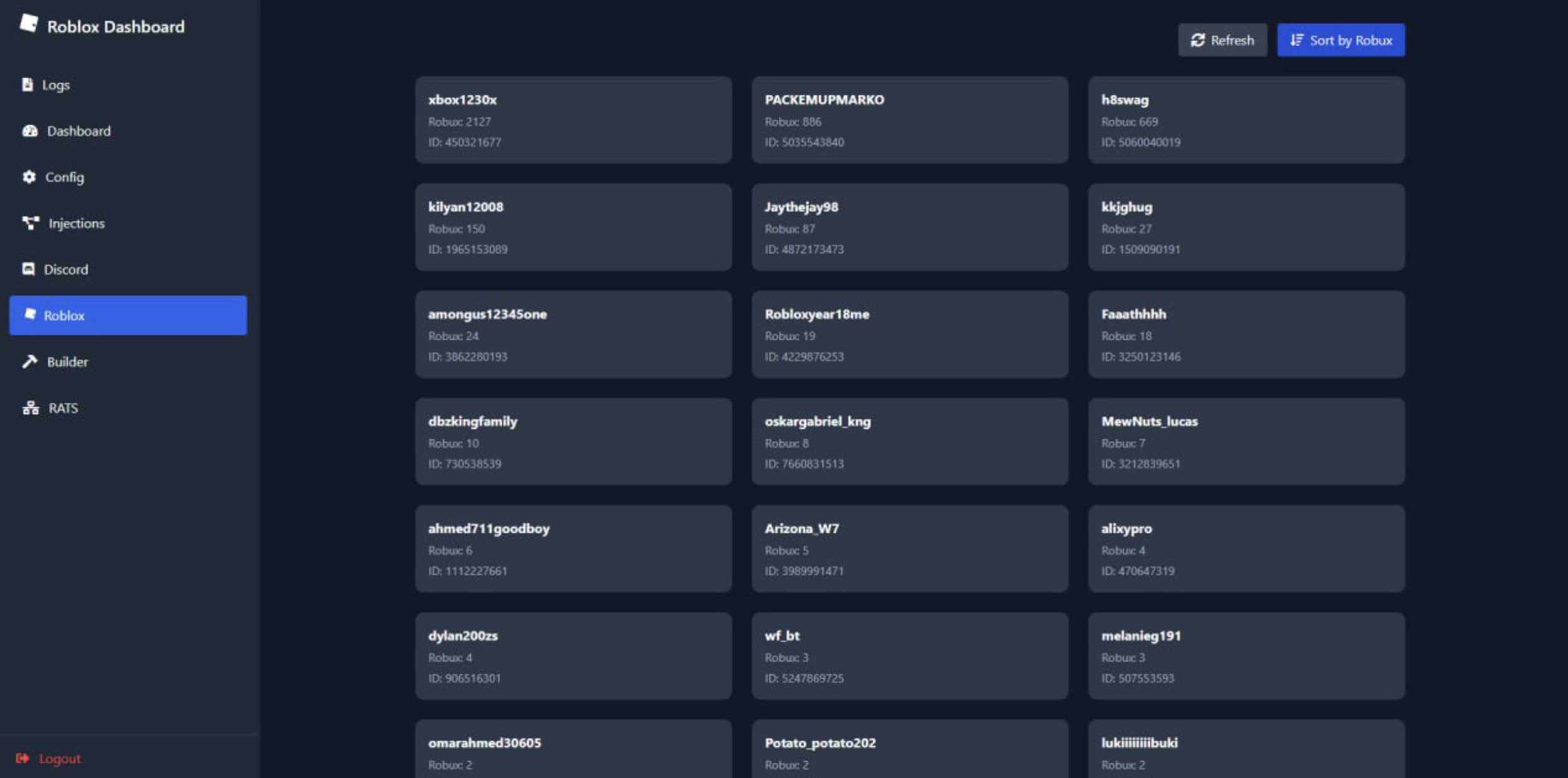
- Crypto wallet targeting: 10+ desktop wallets, 120+ browser extensions
- Decryption for Exodus/MetaMask seeds
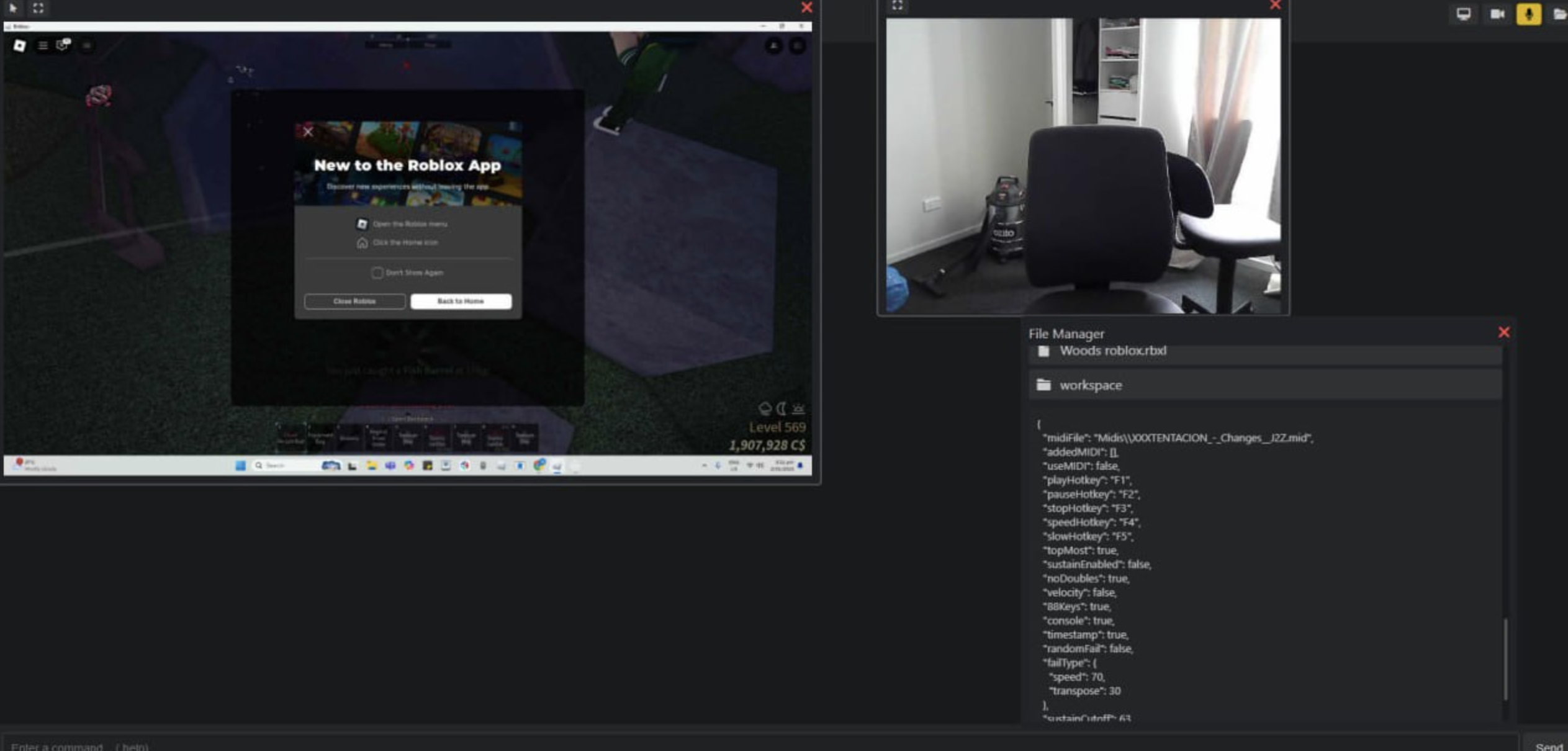
Remote Access (RAT)
- Real-time webcam, screen, and microphone access
- AnyDesk-like remote control
- Live shell with 40+ commands
Ransomware
- LockBit-inspired encryption (claims 100k files/minute)
- System lockdown with custom messages
- Disk overwriting and DDoS capabilities
Notable Commands
.encrypt / .decrypt (key)- File encryption.lockdown (message)- Lock system with custom message.nuke- Overwrite main disk (unbootable).ddos (target)- DoS attack.screamer- Max volume screamer for 3 seconds
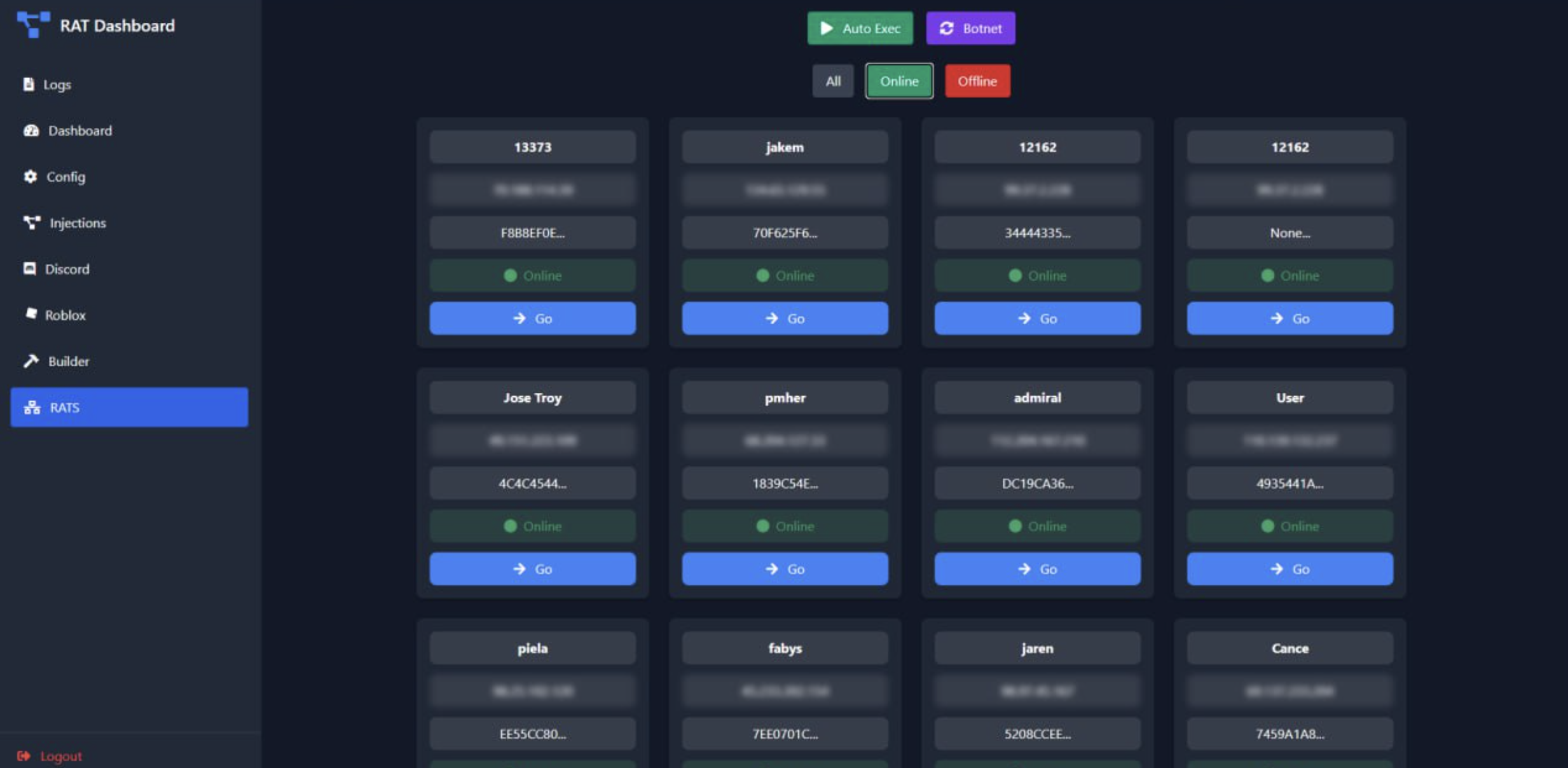
Control Panel
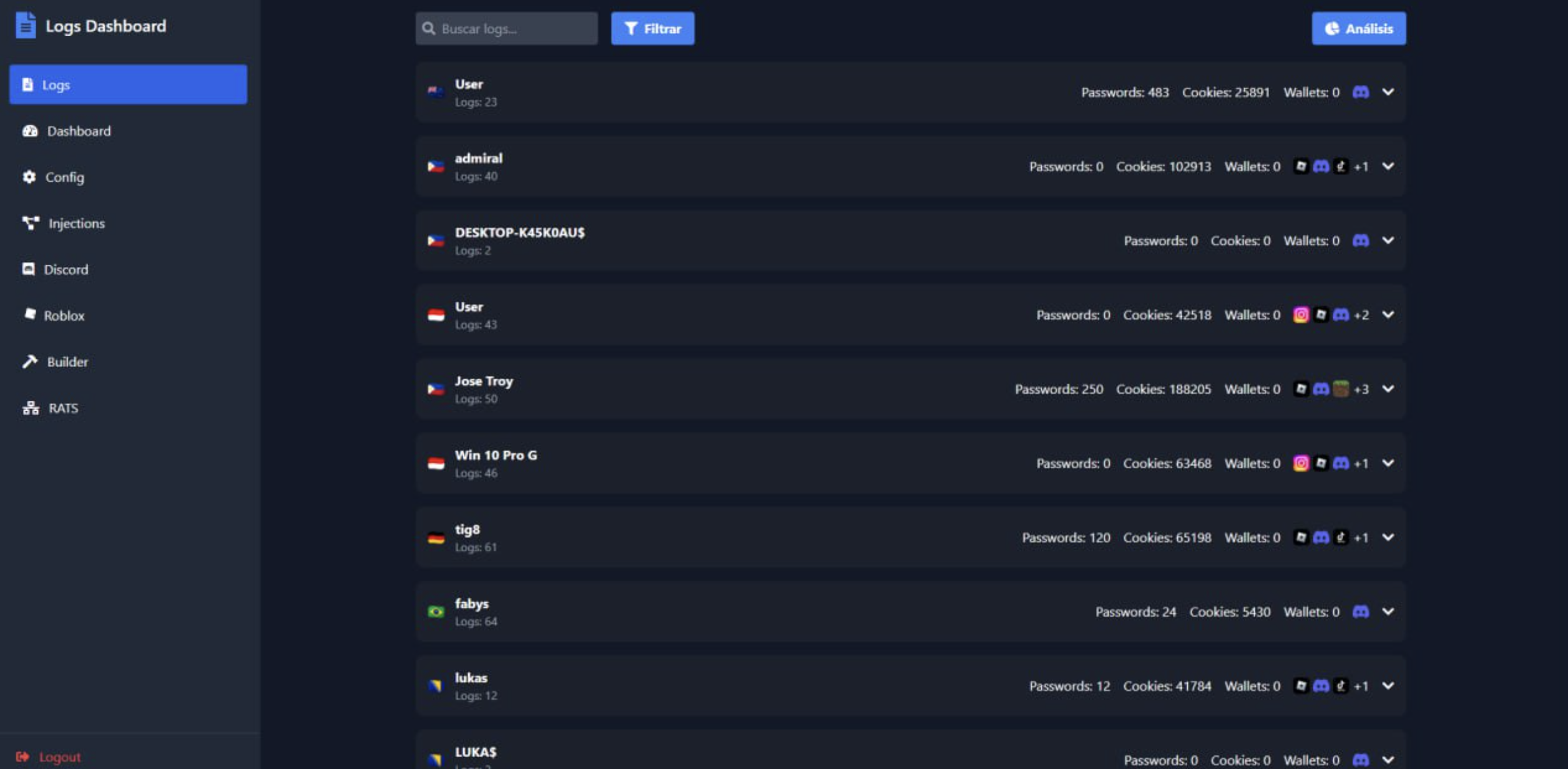
The web-based dashboard displays infected systems with online status, allowing operators to establish remote connections with a single click.
Ransomware
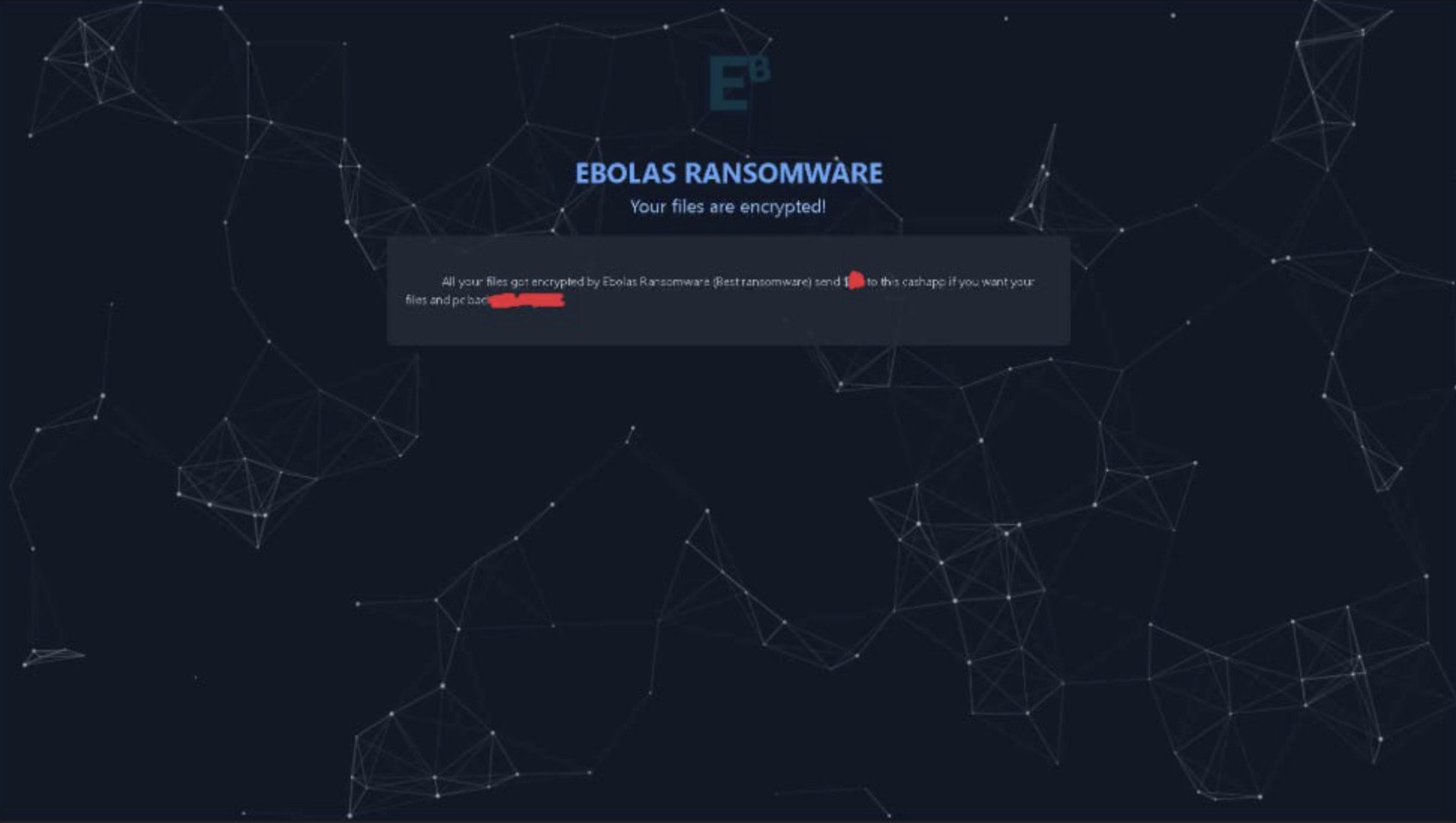
When activated, victims see a branded lock screen with encryption notification and contact instructions. The malware also modifies the boot process to display a DOS-style ransom note on startup.
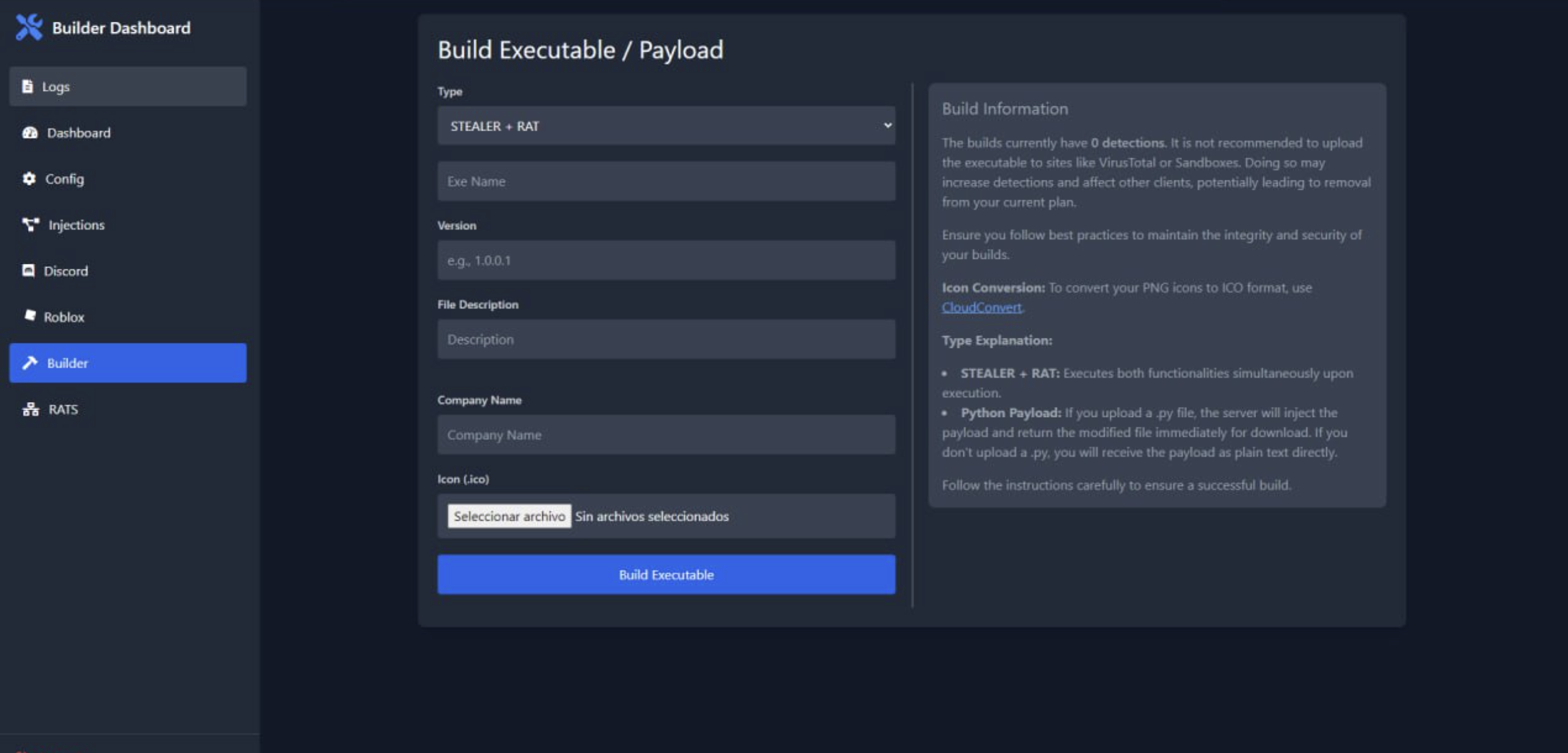
Builder & Configuration
The builder allows operators to customize payloads with combined STEALER + RAT functionality, custom icons, version info, and Python payload injection.
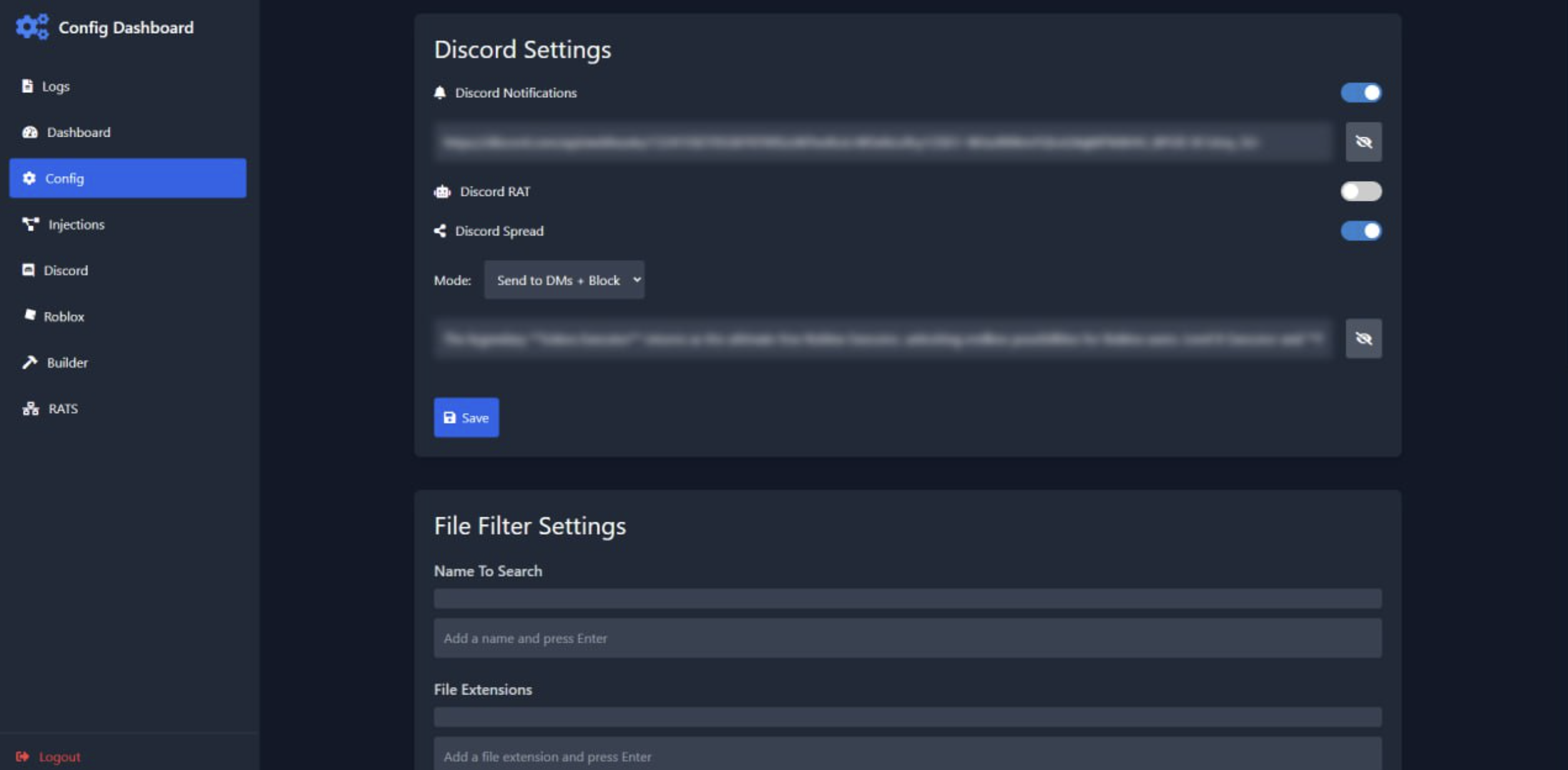
The author claims anti-analysis measures including honeypots, fake injection points, and deliberately leaked builds to waste researchers' time.
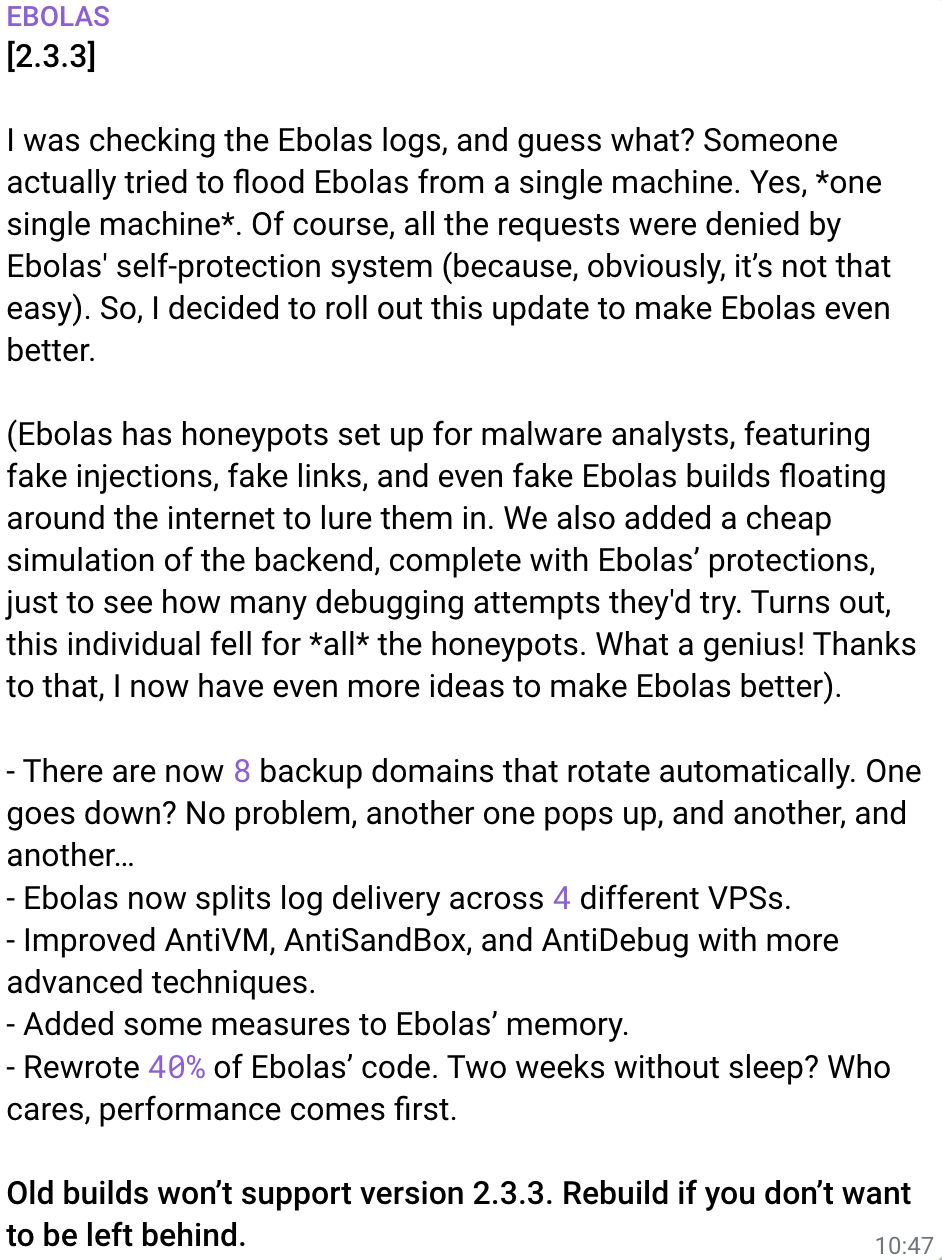
Important: These anti-analysis claims are unverified. Threat actors often exaggerate capabilities to deter analysis.
Recommendations
Tip: Proactive defense significantly reduces risk from hybrid threats like Ebolas.
- Deploy EDR solutions with behavioral detection
- Enable MFA on all accounts, especially crypto wallets and Discord
- Maintain offline backups to mitigate ransomware
- Monitor for suspicious persistence mechanisms
- Train users on social engineering and suspicious files
- Implement network segmentation
Conclusion
Ebolas Stealer represents the concerning trend of hybrid malware combining infostealer, RAT, and ransomware capabilities at an accessible $15/week price point. Its comprehensive feature set lowers the barrier to entry for threat actors.
While some advertised features remain unverified, the threat highlights the ongoing need for robust security measures and continuous monitoring of emerging malware trends.